Cloud Native Ecosystem
Data Protection and Management Solutions

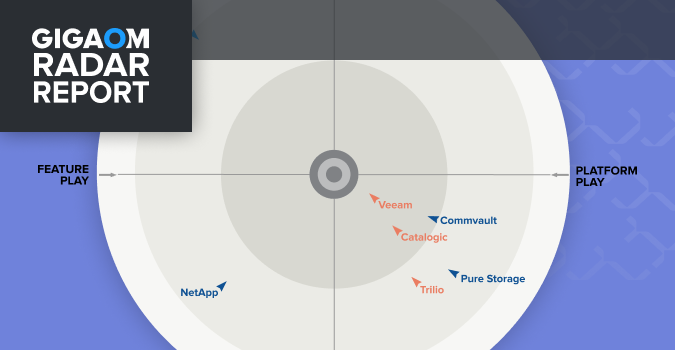
Kubernetes Data Protection Platform
Data
Services
Amazon RDS
Cassandra
MongoDB
 SQL Server
SQL ServerPostgreSQL
MySQL
K8ssandra
Elasticsearch
Kanister
Kafka
EDB
Kubernetes
Distributions
Amazon EKS
EKS-Anywhere
AKS
GKE
Digital Ocean
HPE Ezmeral
Kubernetes
K3S
NKE
Mirantis
OKE
Openshift
SUSE Rancher
VMware Tanzu
Storage
Infrastructure
Amazon EBS
ADS
Amazon S3
Ceph
CSI
Cisco
GCS
Dell EMC
HPE
 Infinidat
InfinidatMinIO
Hitachi
OCI
Lenovo
Zadara
Net App
Pure Storage
Security
Services
Kyverno
OPA
Red Hat
Vault
AWS